



08.
Final Design
Reflection
07.
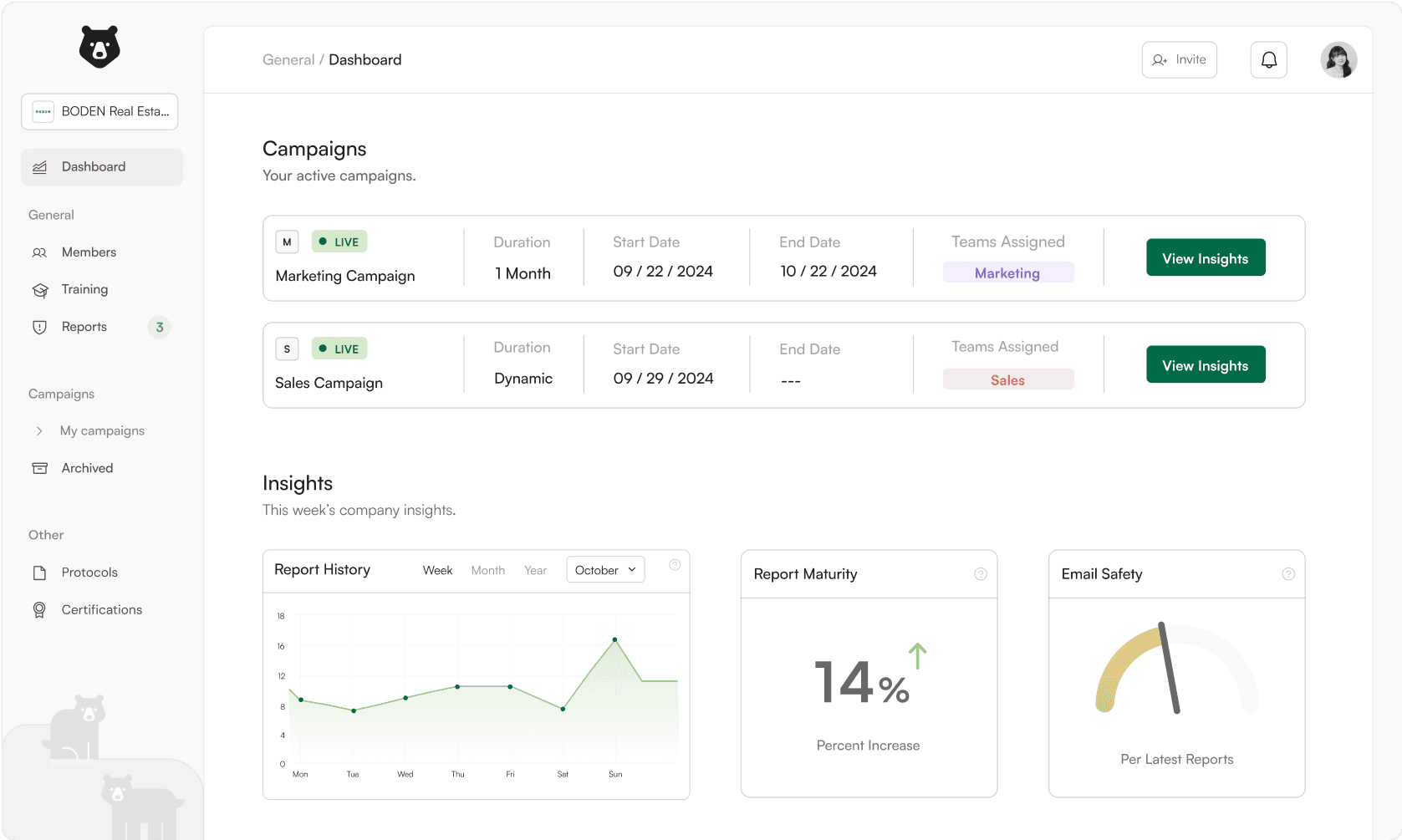
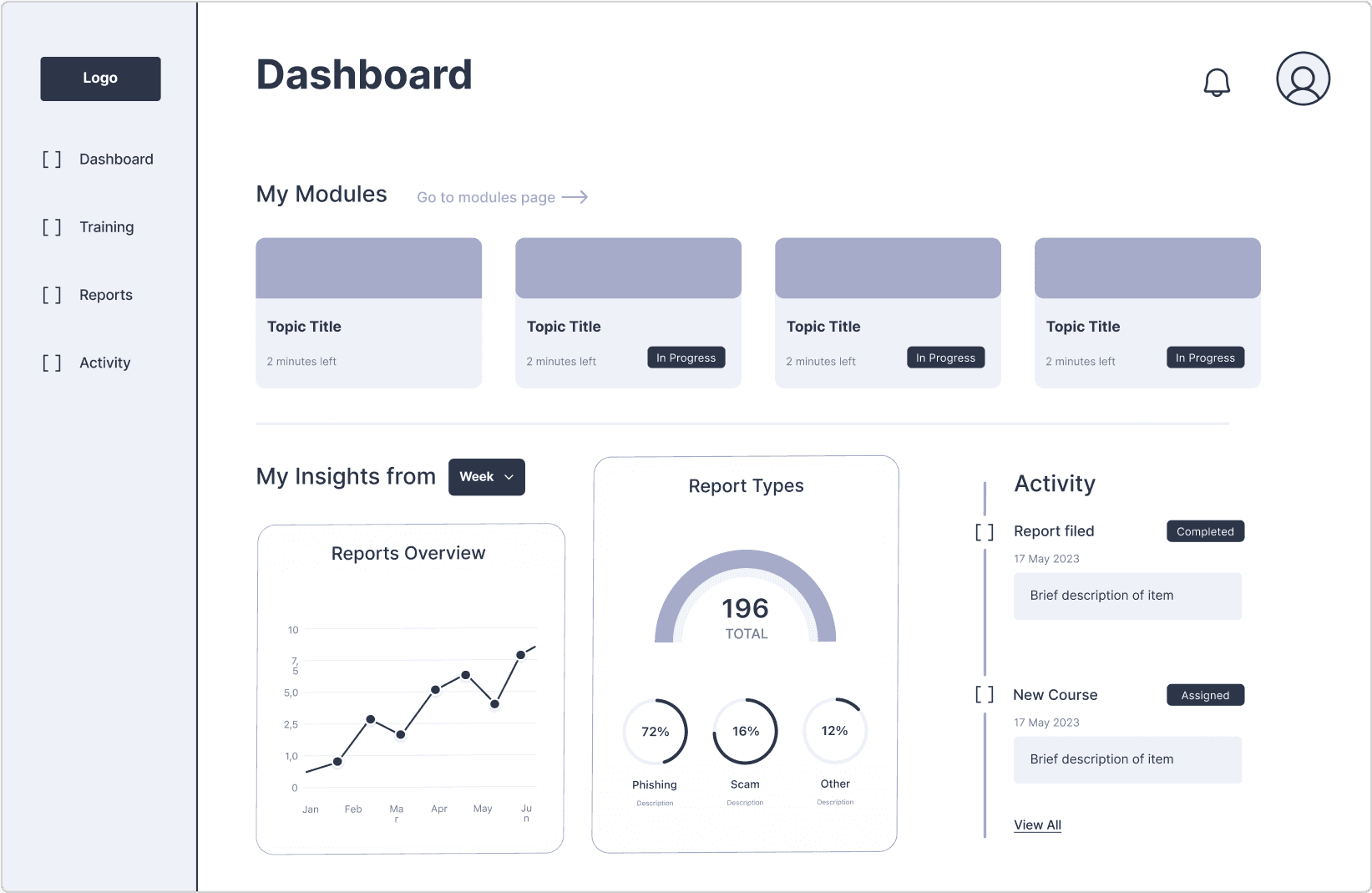
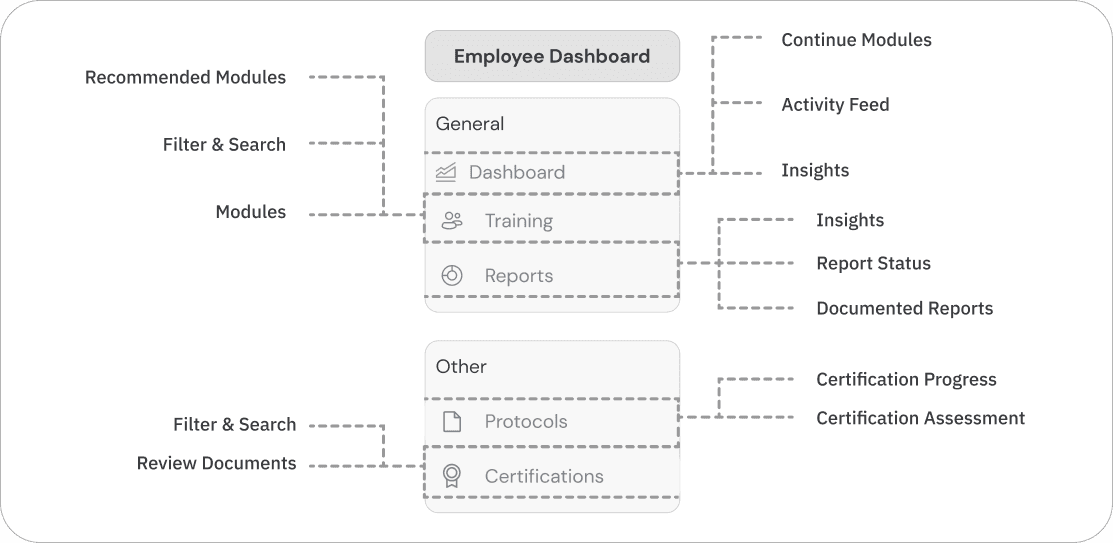
Dashboard
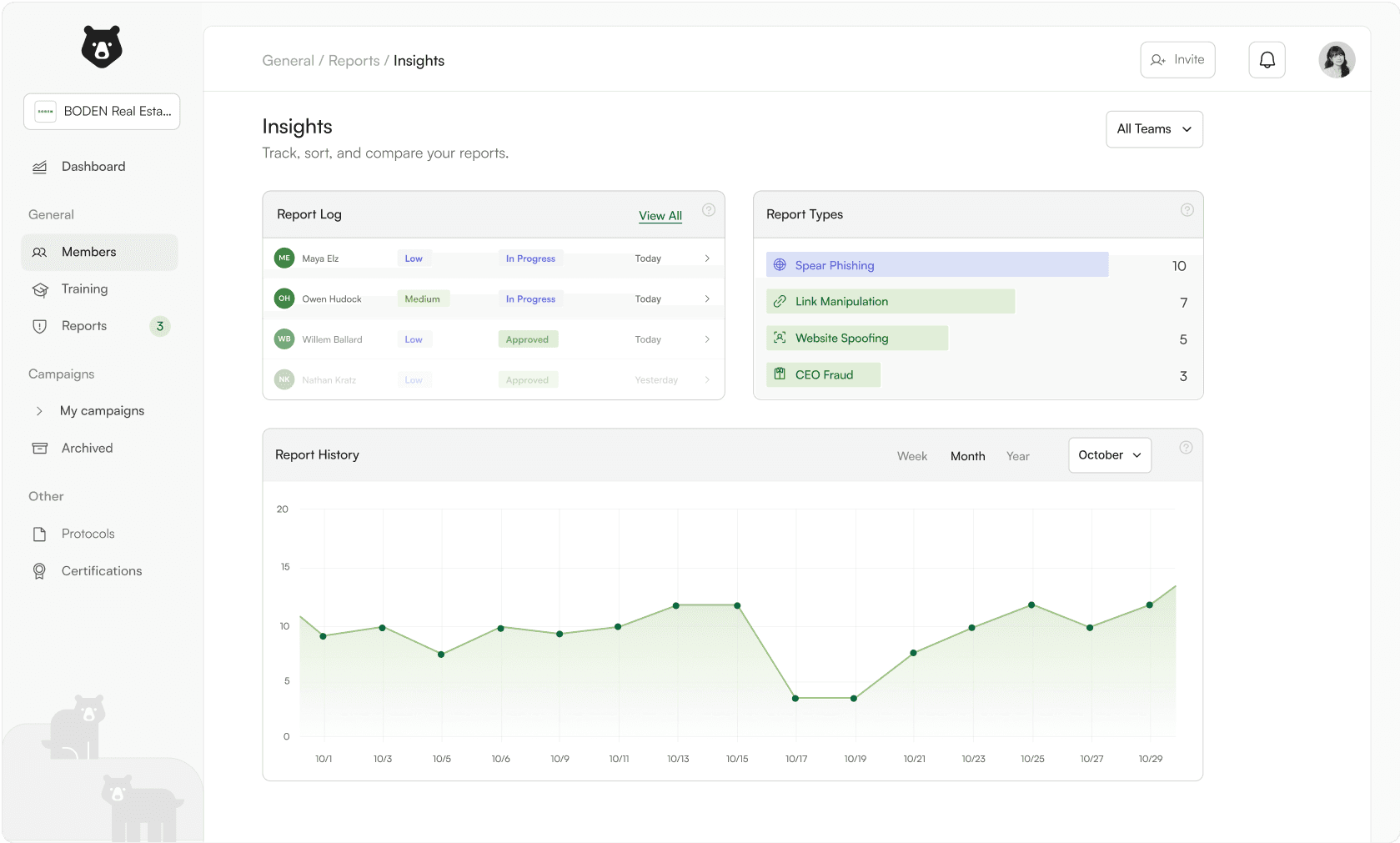
Report Insights
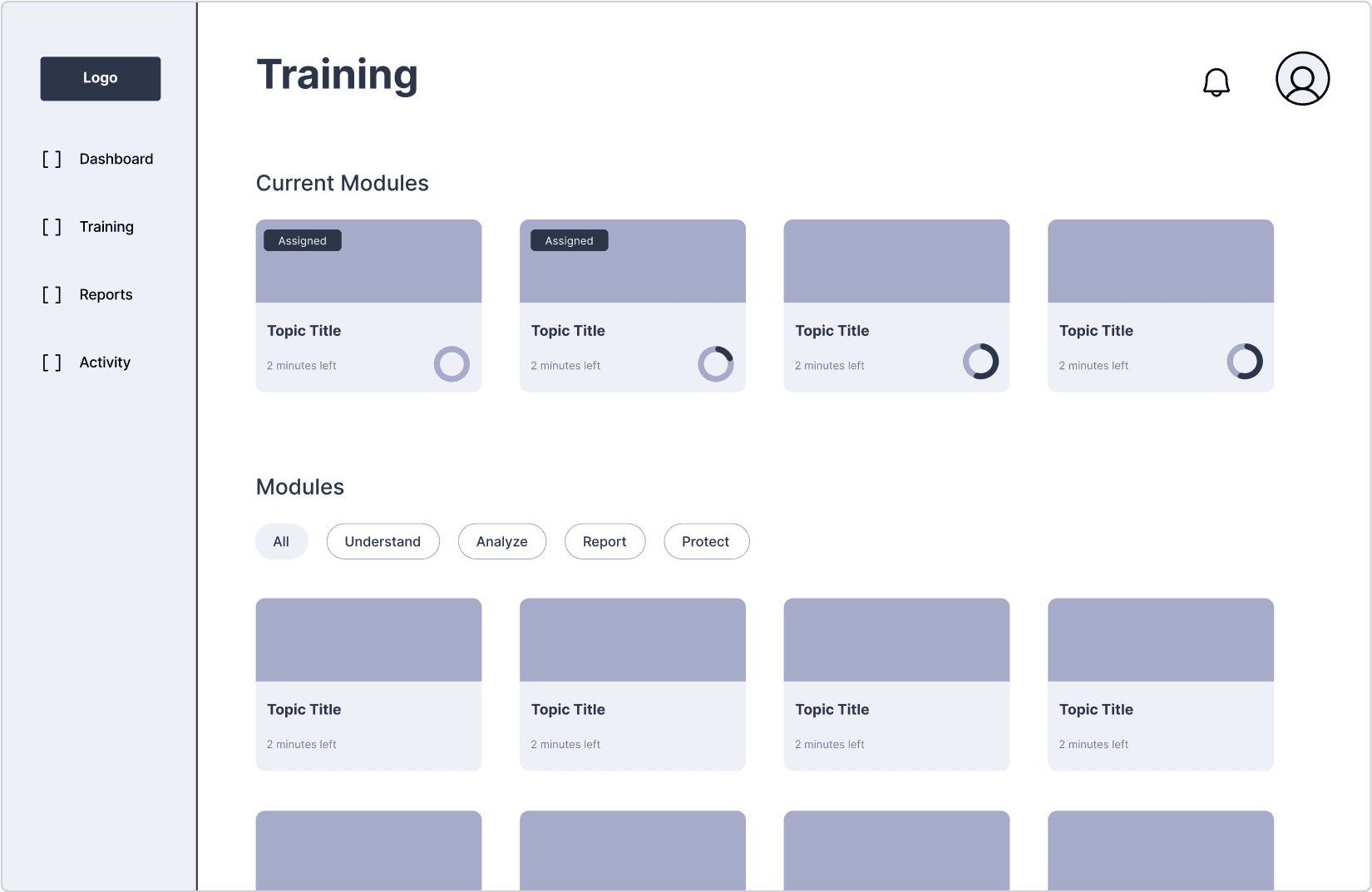
Employee Training
Employee Training Modules
Campaigns
Report Widget
Employee
Employee
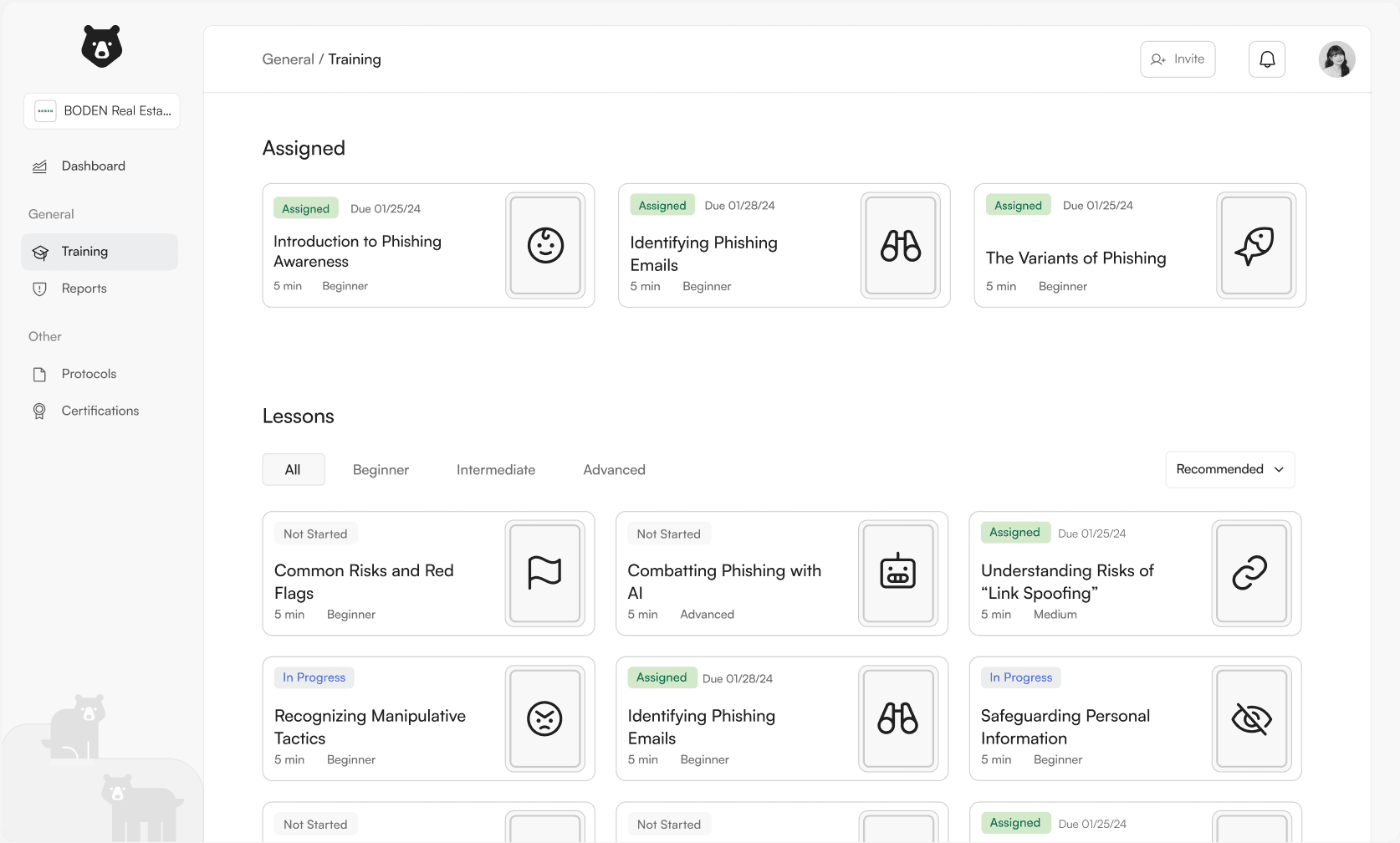
Training Page
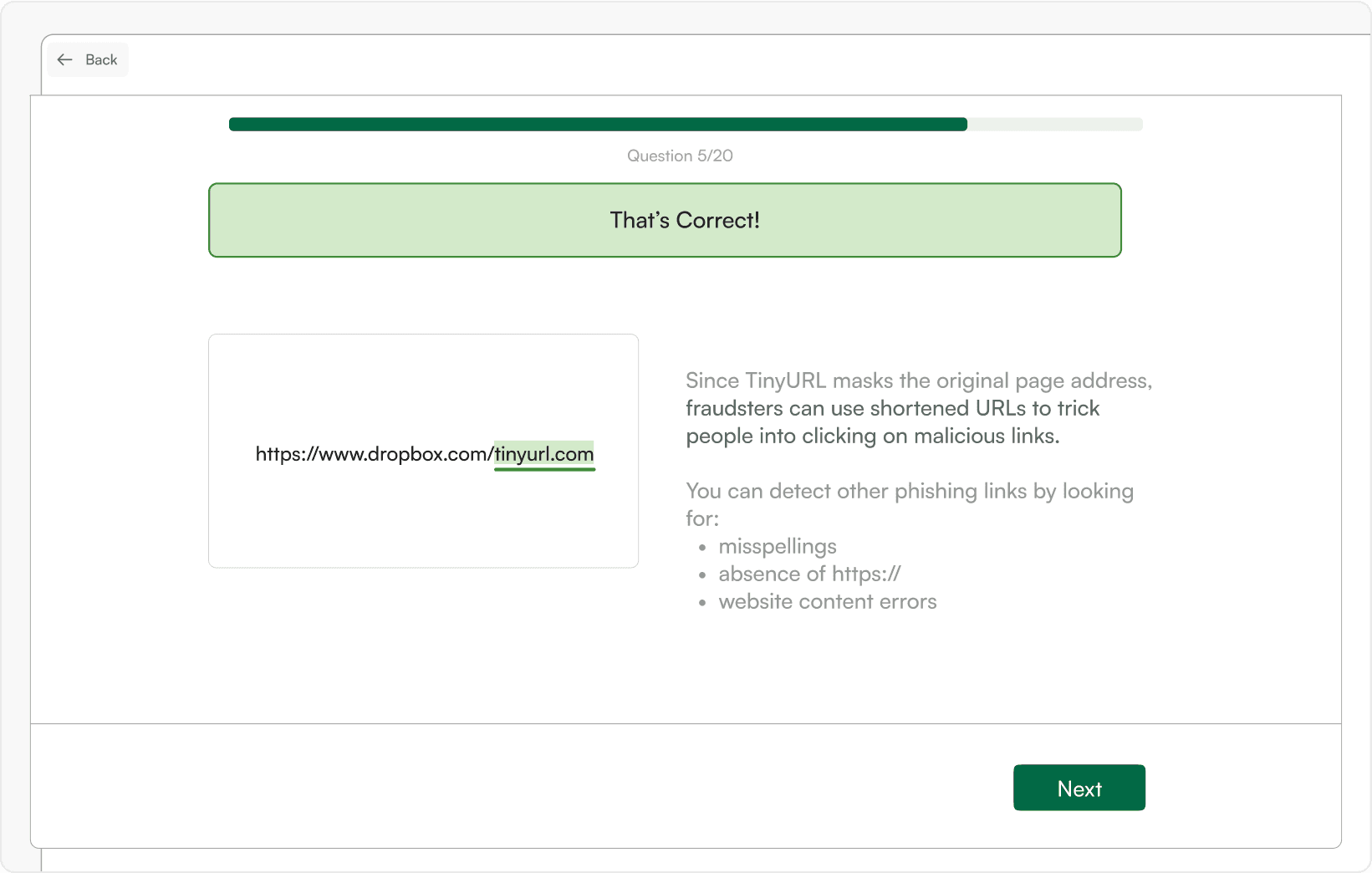
Question
Lesson Complete
Question Answer
Assign Campaign
Inbox Widget
Widget Variations
Campaign Review
Employer
Employer
Training Module
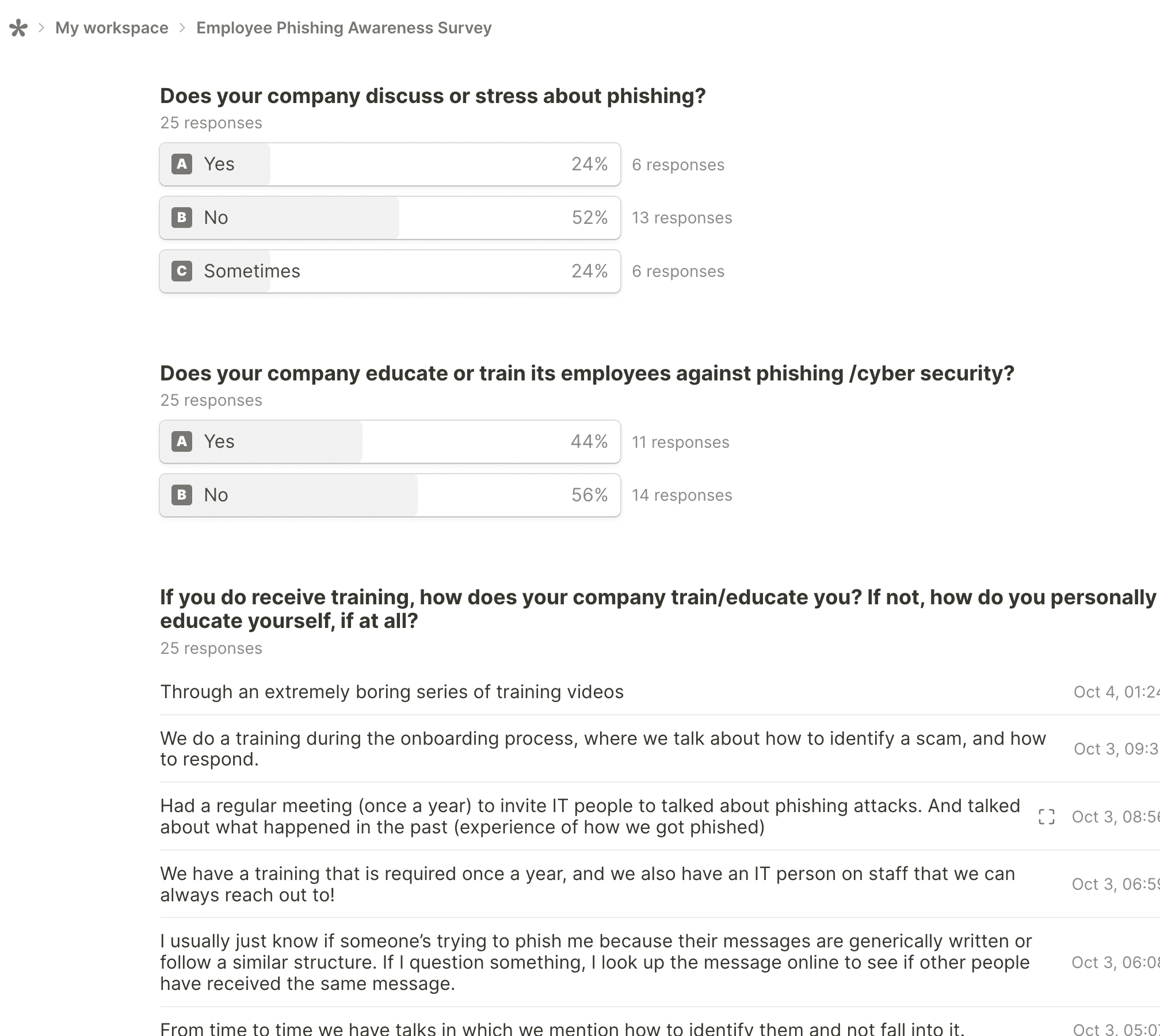
Our landing page starts as the dashboard: a hub for relevant, dynamic information for the user to react with immediately.
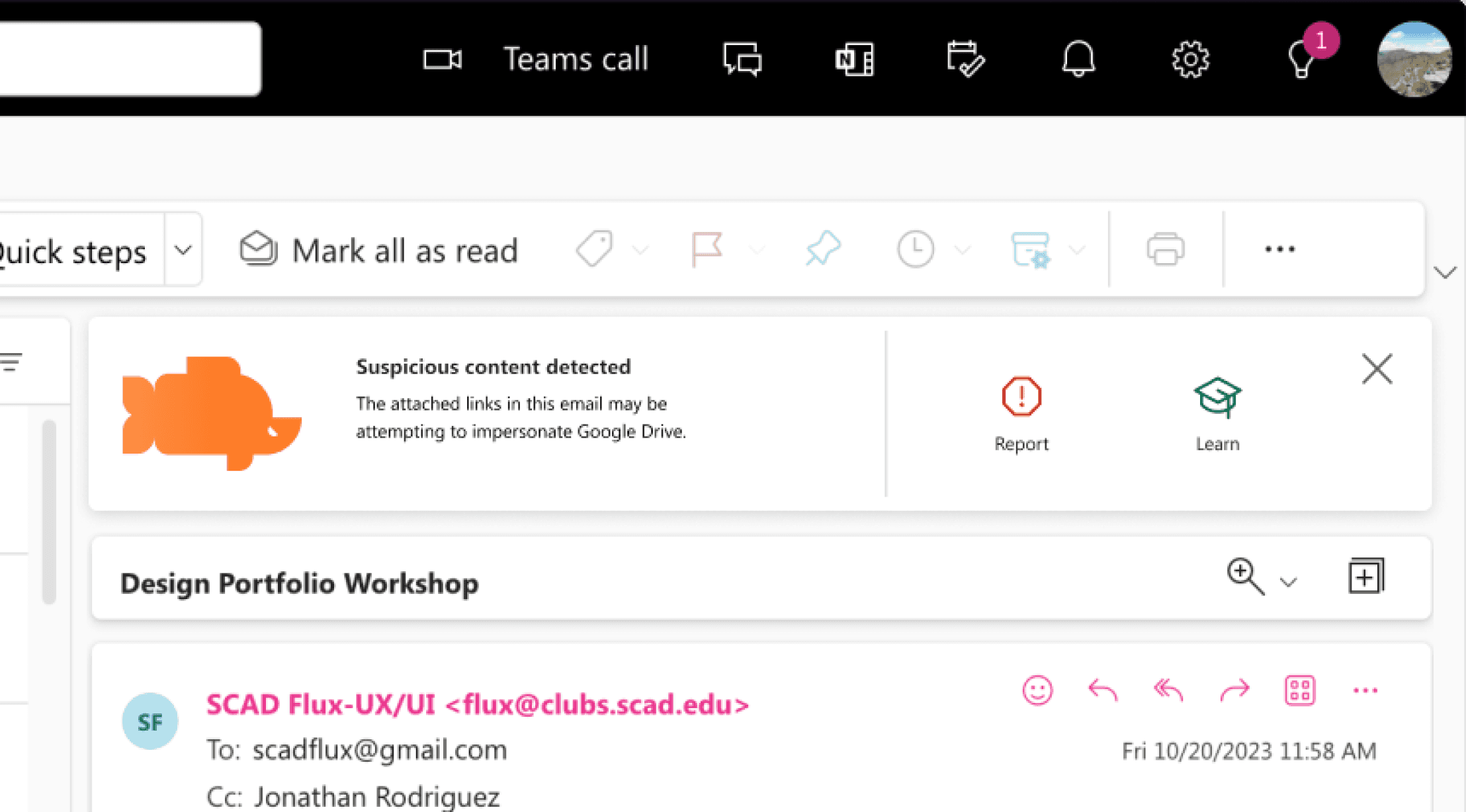
The reports page presents users with a simplified data sheet that updates from the email widget.
For owner’s they can view monitor and approve each report.
For employees, they can see in live time when one of their reports are approved.
Employees can see which training modules have been assigned to them. They can also view and filter through all possible lessons.
Employees take engaging training lessons that educates them on phishing tactics and helps bring awareness to what to look out for when scanning emails.
Employers can set up and monitor phishing simulation campaigns to identify employees susceptible to phishing attacks, thereby strengthening their cybersecurity posture and creating a safer work environment.
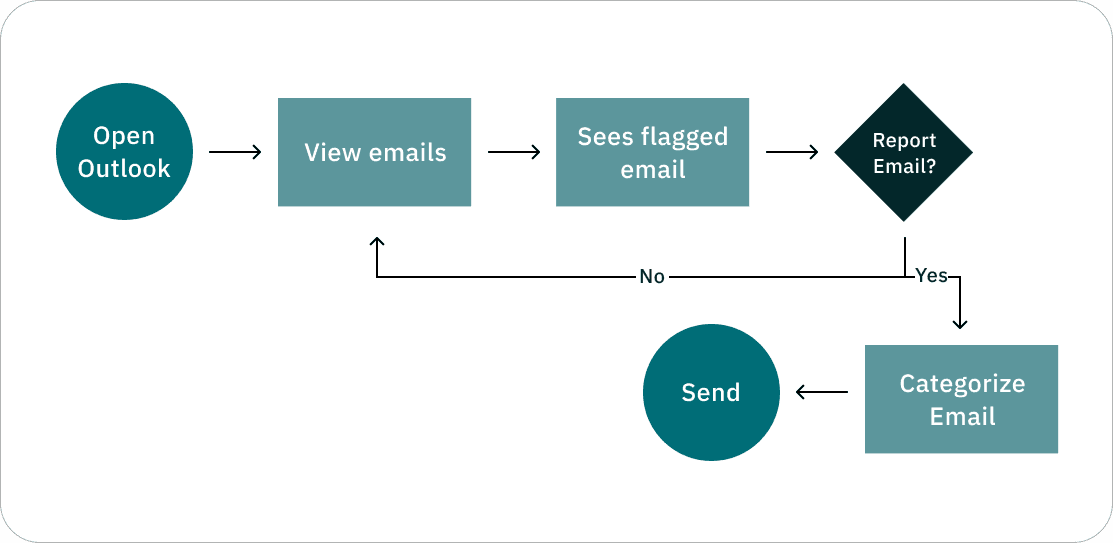
The report widget assists streamlines the reporting process while helping employees validate emails.
During my time as a UX research lead in this course, I gained valuable insights that contributed significantly to my personal and professional growth. Although I enjoyed the subject, researching phishing problems for small businesses and generating innovative ideas beyond existing programs presented a challenging task. Conducting interviews with individuals in the small business field added to these challenges. However, with ongoing discussions with my team, we successfully identified and addressed issues, fostered ideation, and ultimately solidified our concept.
Through this project, I discovered my passion for identifying and solving problems, fueling my enthusiasm for research. Focusing on research and user interviews allowed me to hone my skills. I also learned the critical importance of communication, active listening, and respecting teammates to foster a collaborative environment.
This journey not only shaped me as a UX designer but also as an individual and a supportive team member. Despite the challenges, I found every moment of this project rewarding, particularly when we, as a team, successfully overcame obstacles.








Low-fi and Usability test
Branding Production
05.
06.
In this project phase, our team aimed to create a preliminary prototype with minimal detail for our product while also engaging in user assessments.
We have considered these three factors in selecting the pages.
After multiple design iterations, my team identified these key screens for low-fidelity UI designs. We then proceeded to conduct usability testing.
We've reached an exciting stage where our functional prototype is prepared for user testing. I've conducted usability testing with individuals from within the company, aiming for a seamless experience for both employees and employers.
I analyzed and organized the gathered feedback and insights. This provided valuable input to support the final UI design and interaction development.
We were able to interview employees who work in the industry and gain valuable insights into how this could integrate into their work flow.
Having industry employers provided us with insightful feedback and gave us a better understanding of executing this process with professional implementations in mind.
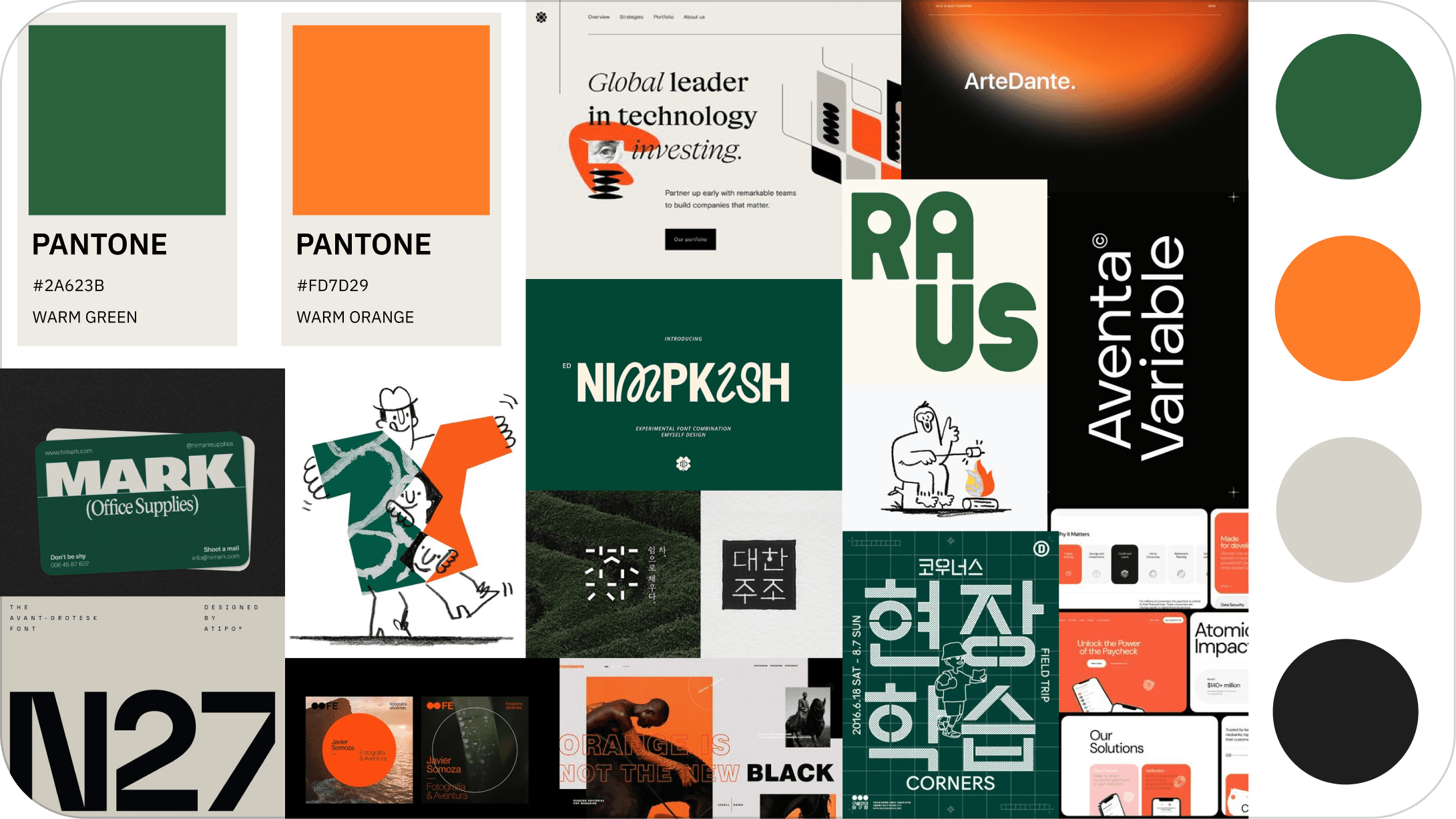
We began our mood boards with three key words in mind: Innovative, Loyal, and Energetic. From there, we drafted colors, images, and typography around the ideas our words elicited.
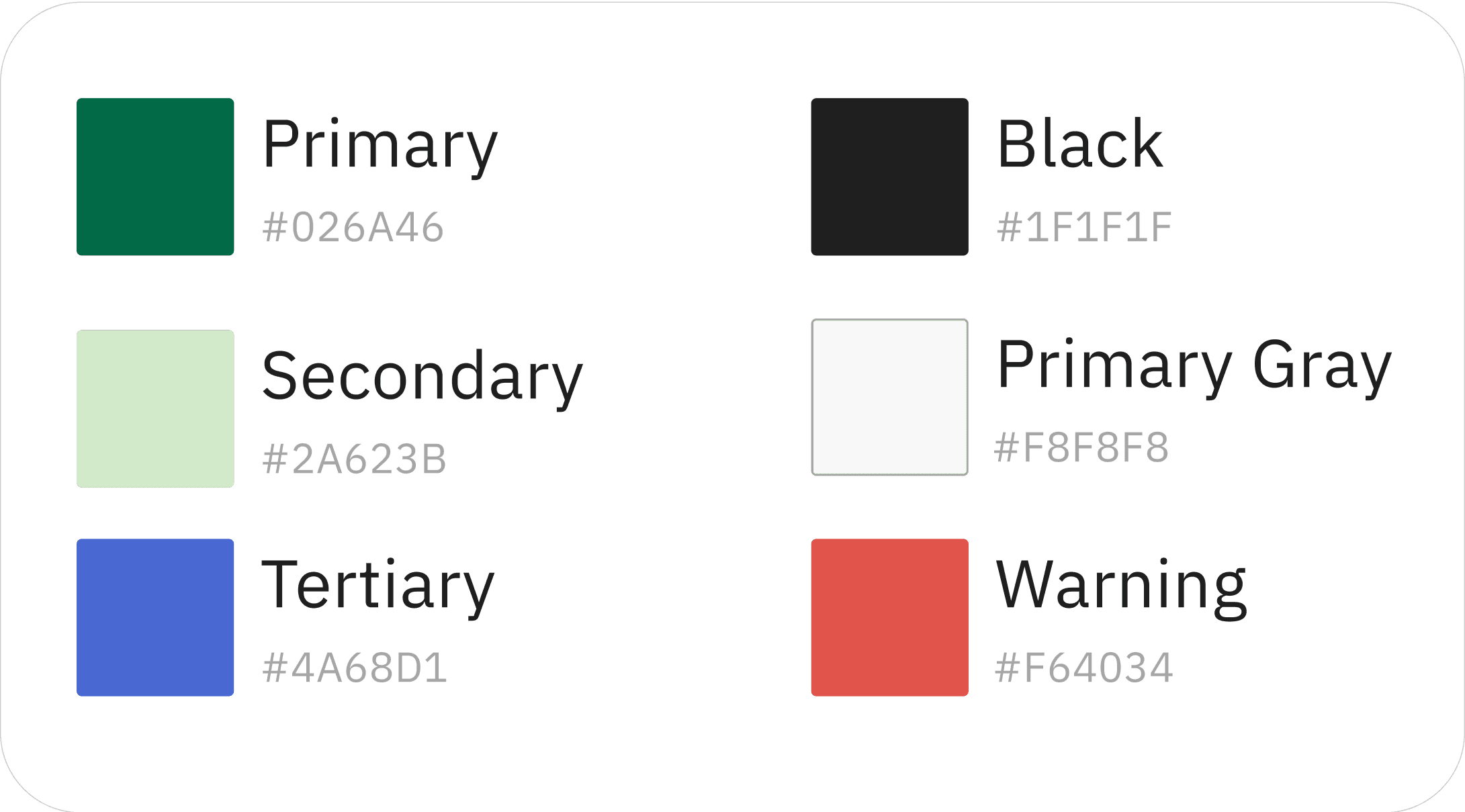
My team was inspired by both our mood boards and accessibility guidelines, leading us to decide on a simple and limited color palette.
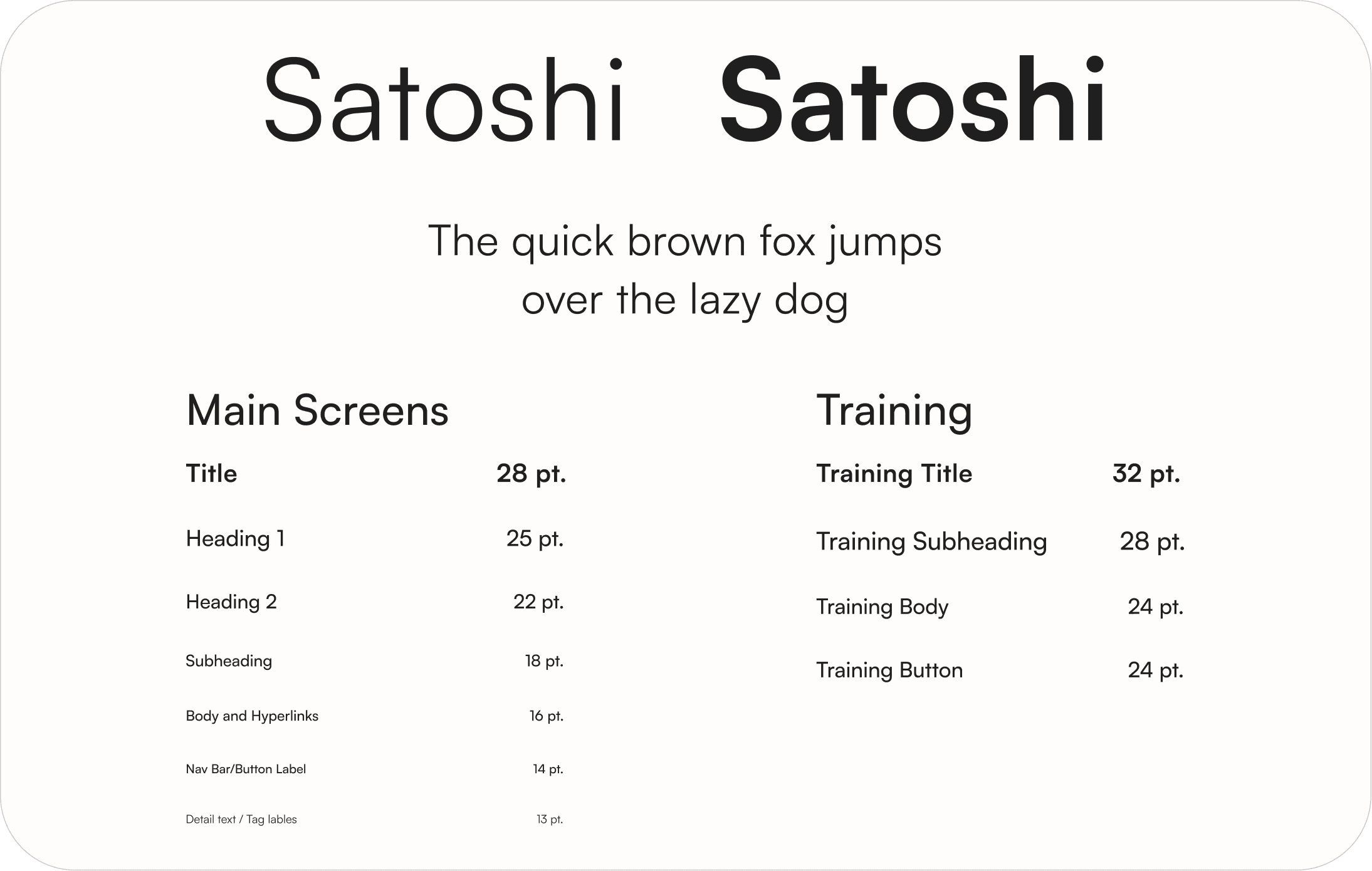
We conducted a type study to determine our typeface for our UI. We evaluated over 20 typefaces, testing them at different sizes and weights.
We chose a bear as our primary logo. Our goal was to create a simple logo that would be readable at various sizes.
Our key takeaway from this round of user interviews was how we could improve our visual communication and provide a clear user journey.
Low Fidelity
Usability testing
Moodboard
Color Palette
Typography
Logo Branding
Employee Feedback
Employer Feedback
Visual organization



Simple Design
Clear User Flow
User-friendly
Information Structure
Conducted
15 of A/B testing
6 Usability testing
2 Expert
Evaluation
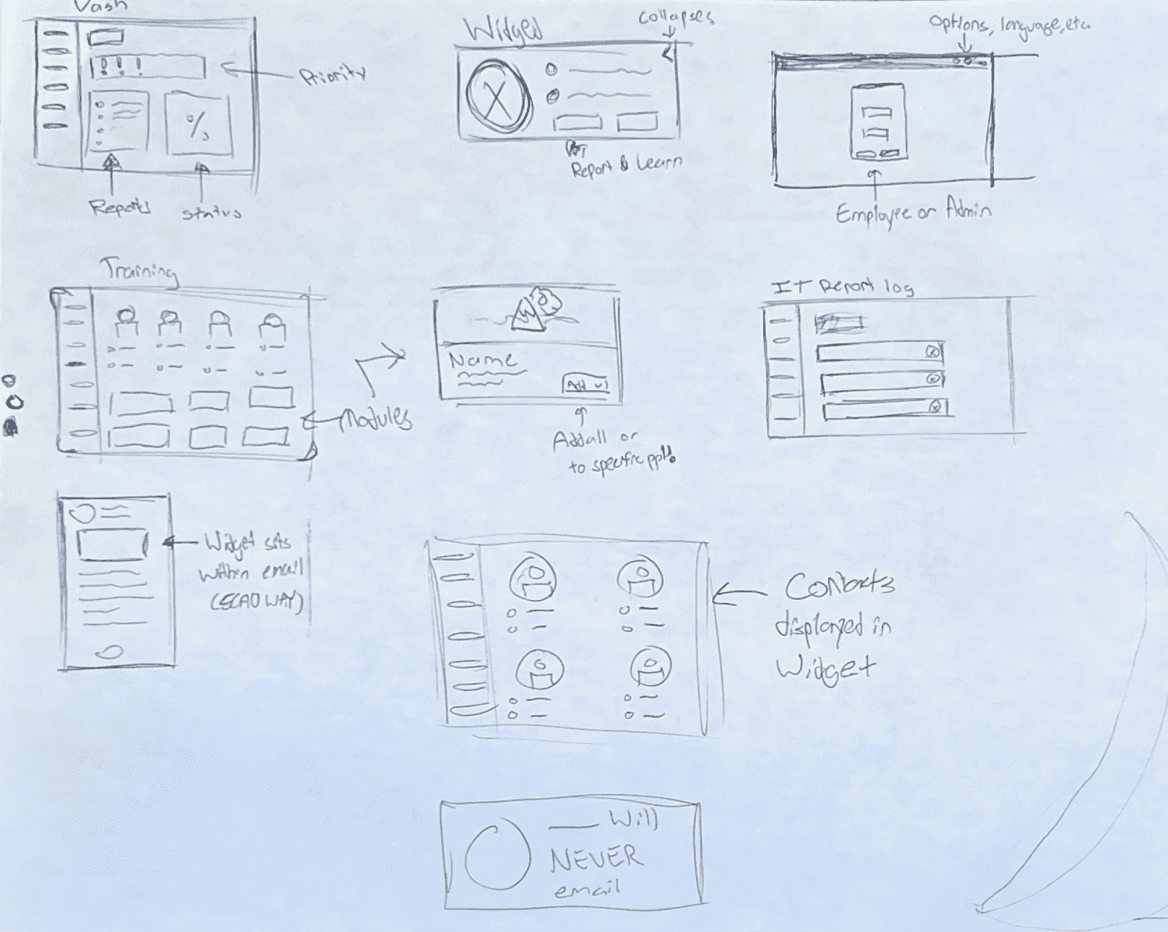
Before getting into low fidelity development, we had an ideation session to brainstorm every possible feature for our product.
Our team ideated different ways to visually display different features.
We reviewed our Feasibility map to help support which features to focus on.
Each team member made their own ideations of how they think the UI could be visual displayed
Feature Ideation
Idea Dump
Feature Feasibility
Lo-fi Sketching
Employer Flow
Email Widget Flow
Key Features
User Flow
04.


Impact
Feasibility



Employee Flow

Monitoring Platform
Reporting Widget
A desktop-preferred interface that allows business owners and employees to interact with their report history, essential documents, training material, and overall company safety.
An integrated extension that embeds into any email provider via HTML integration. This ensures live tracking of filed reports and campaign simulations.
01.
02.
After completing our personas and empathy mapping, we created new POV statements.
Connecting our HMW Statements back to our UX Stakeholders.
Our team conducted a competitive analysis on a range of products and companies who provided email scanning and other cybersecurity services. Apart from documenting their services, we also looked at their branding and interfaces to see what we could improve upon.
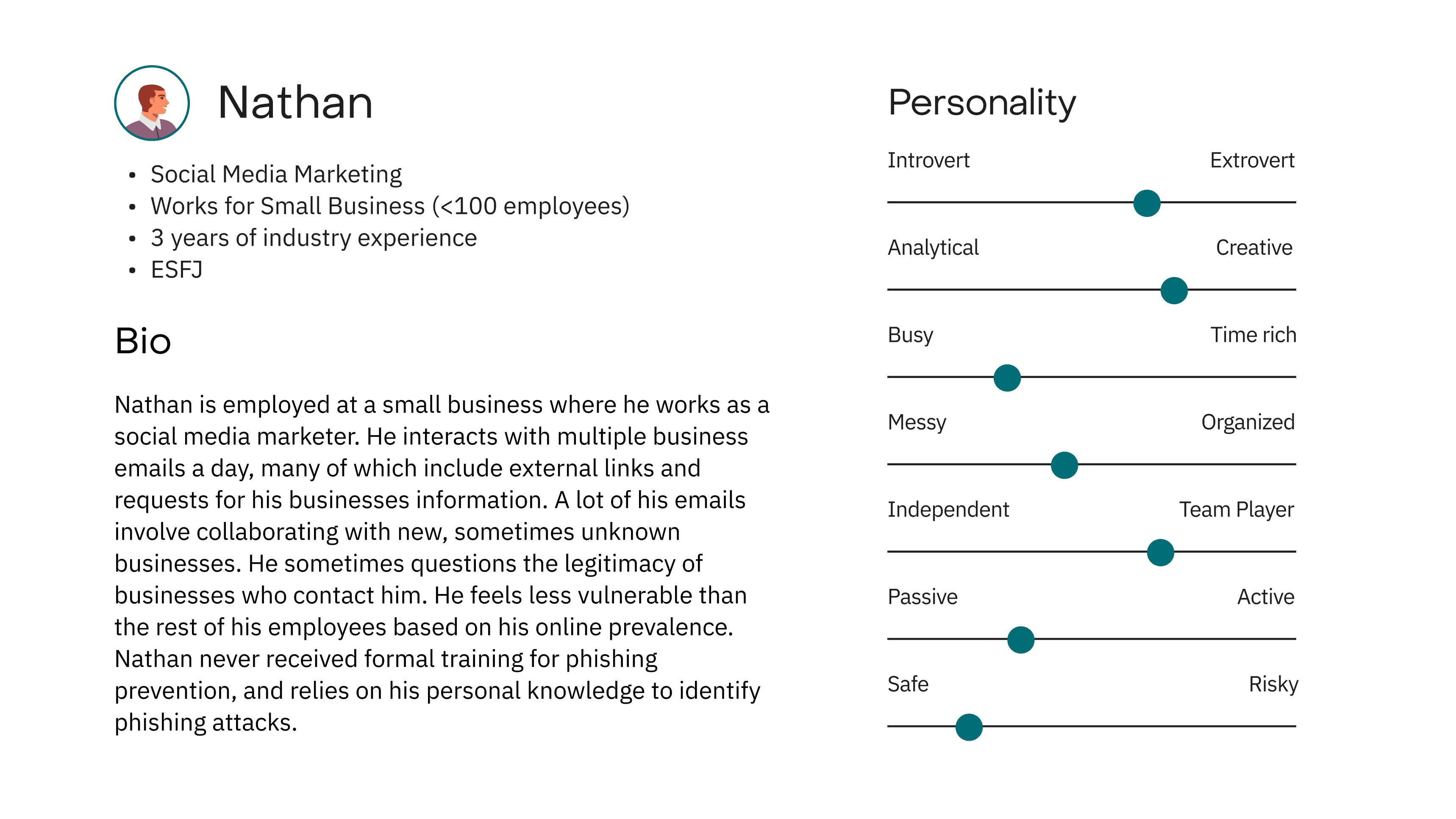
An employee who has a stressful workload with lots of email communication, and who is unengaged by phishing training, needs a proactive system that helps him take care of phishing detection and reporting because he wants to focus on his tasks and be productive.
An employee who worries about their security , needs confirmation and communication of trust that her reports are effective and will not negatively affect her because she is fearful of her vulnerability in the company and as a potential phishing victim.
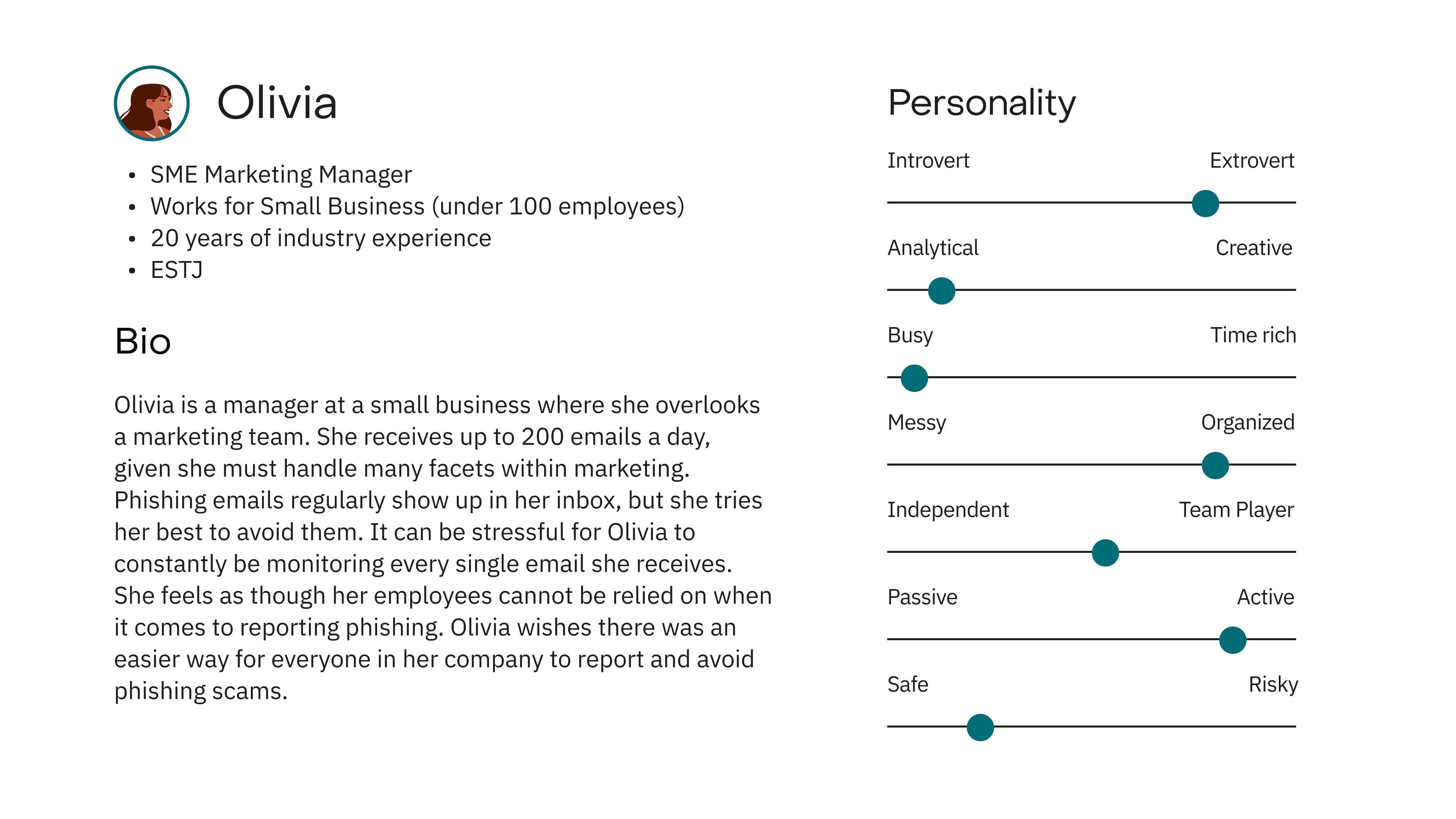
A manager who sees her employees as potential liabilities to the companies safety, needs a trustworthy, reliable system that can aid employees with proactive and passive solutions, because it increases the companies safety and reduces workload.
POV statement
Creating our Framework
Competitive Analysis
Nathan
Maya
Olivia


After defining our personas, crafting POV statements, and gaining a comprehensive understanding of our problem space and target audience, we finalized our HMW statements.
How might we engage employees in phishing awareness without distracting them from their priority tasks?
How might we alleviate stress of navigating phishing reports for small business owners through a more simplified process?
How might we make the process of conducting phishing reports more approachable to increase employee confidence?
How Might We statements
Personas

During this phase, my team and I conducted primary research, developed personas, and created "how might we" statements.
We, along with our teams, employed three primary research methods to answer this question by identifying our target interviewees: employees, owners, and cybersecurity experts.
Our team conducted affinity-mapping to group similar sentiments to filter common pain points and needs from both employees and owners. We conducted four rounds of affinitization and finalized with six key statements
After identifying six key insights, we created multiple point-of-view (POV) statements that examined the problem from a broader perspective incorporating each insight. These statements were then used with our personas to create new identities reflecting these perspectives.
Survey results showed overall that over 60% of employees have some form of a cybersecurity program within their company. But out of the 60%, only 40% are actually satisfied with the training they receive.
My teams and I conducted both in-person and online calls with employees and owners, using pre-established scripts for guidance. Following the interviews, we organized and consolidated data points for affinity mapping, grouping stickies based on similar sentiments.
All insights generated from the session were separated from our affinity-mapping process to be later grouped and aligned with our 'how might we' statements.
25 participants
2 Interviewees
These interviews aim to gain a deeper understanding of our research insights, quantify our data, and connect with employees from small companies with varying expertise.
Our 5 W’s
Primary Research
Research Consolidation
Affinitization
POV statements
User Survey
User Interview
Subject Matter Experts
When does the problem occur?
When employees interact with emails and other messaging systems
Who is affected by the problem?
SME Owners (client) and Employees (end users)
Why does the problem occur?
SMEs view their employees as potential liabilities rather than their strongest assets against phishing.
Where does this problem occur?
Through employee emails and messaging systems received in office or remotely
What is the problem?
SMEs are frequent victims of phishing attacks but fail to report over 70% of received phishing threats


Define problem space
03.


12 Interviewees
Our focus initially rallied behind the idea of cybercrime, based on personal sentiments, but continued to research further into other quadrants of security that we felt connected to.
01.
Our team decided to focus on phishing, and began to narrow the problem space to focus specifically on small businesses, who are the most detrimentally effected by attacks. However, we still needed to understand why small businesses face these staggering numbers.
Initial Ideation
Our Solution
Create a platform that assists small businesses in becoming more aware of phishing threats.
This course explored the physical, psychological, and behavioral characteristics of humans. Our goal was to apply these concepts and develop a usable, desirable, and effective product in a 10-week time frame.
Persona development and user interviews
Low fidelity designs and design analysis
Finalize hi-fi designs and brand strategy
Define
Design
Deliver
Discover
Secondary and market research of topic
How Might We...
How might we create a cybersecurity framework that builds employee confidence in identifying and reporting phishing threats while fostering trust for business owners?
We followed this 4 step process for our project, which went along with the 4 presentations we have to give throughout the quarter. This allowed to set clear expectations for our project roadmap.
Overview
Our Process
00.
Only 15% out of 3.4 billion phishing emails are reported, with the other 85% putting small businesses in threats.
Problem Statement

A desktop application designed to heighten phishing awareness for small businesses.
ursa
Fall 2023
10 Weeks
Product Design
Research Lead
Human Factor
Figma
Sejoon Kim
Info Arch
Lucilla Fell
Belle Duffner
Owen Hudock
My role:
Scope:
Tools:
Team:
In our secondary research, my teams and I aimed to identify pain points, comprehend current market trends, and pinpoint our target audience. While conducting the research, I discovered similar websites and analyzed their content, comparing it with our goals. Subsequently, we delved into researching potential target audiences.
Small businesses face a persistent challenge in the form of phishing emails.
They have to constantly safeguard their data and resources from these attacks. Despite implementing security measures, it is difficult to achieve comprehensive protection as phishing attacks directly target individuals.
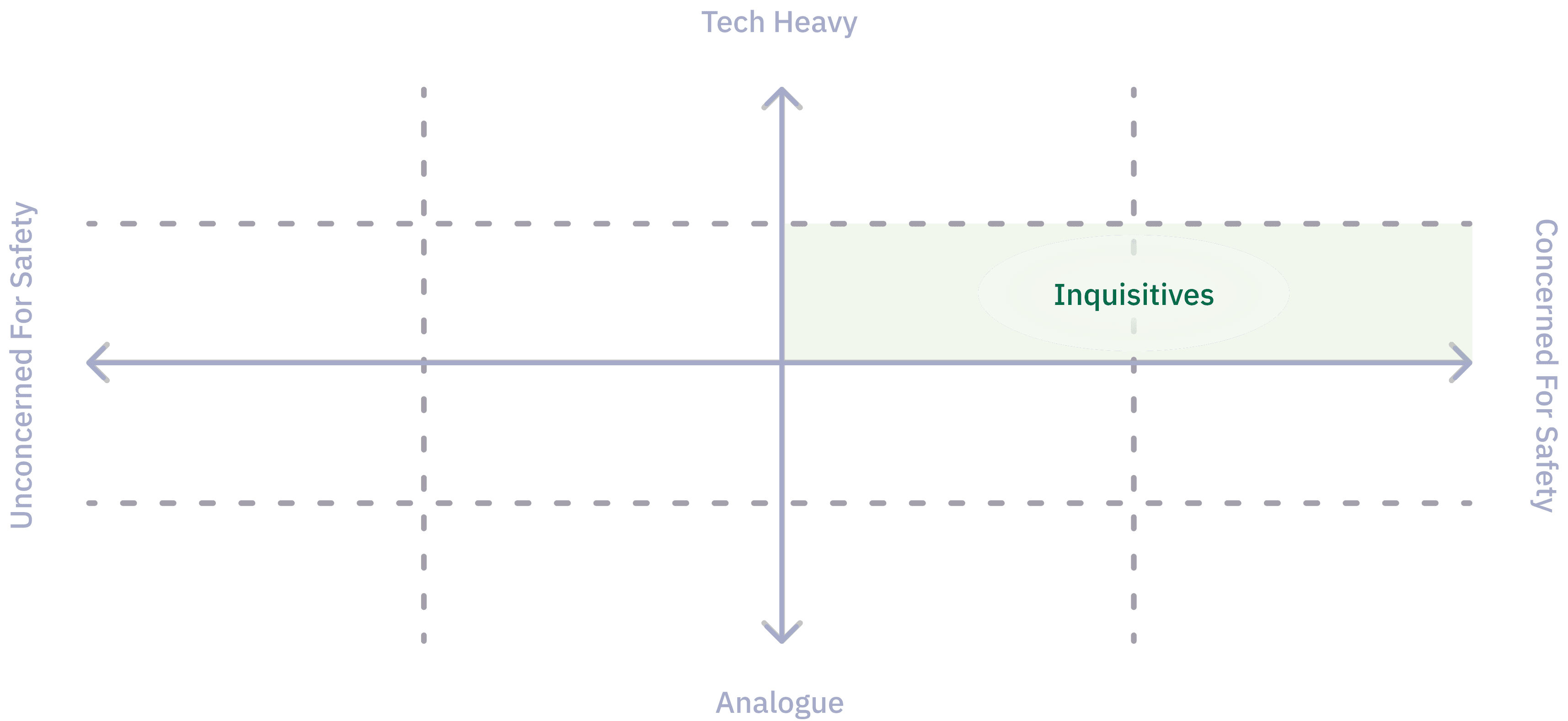
Not every small business applies to our problem space. So, in this case, we defined our audience to be the archetype of “inquisitive”– those who function in a business that is more technology heavy and have higher level of concern for company safety.
Our initial goal was to determine how to provide small businesses the proper support to monitor, report, and document phishing attacks.
By increasing company’s ability to report and identify phishing attacks.
Phishing or ransomware attacks occur every 11 seconds.
Phishing is the leading attack against small businesses by over 25%.
By collecting meaningful data that can, in turn, create more effective training solutions.
Demonstrate your company’s efficiency and safety by state and industry regulated and recommended compliance measures.
Small businesses are the most frequent victims of cyberattacks, but only 15% of attacks go reported.
Research Phase
Key Findings
Overall Finding
Defining our Target Audience
Initial Goal
Reduce Risk
Increase ROI
Maintain Compliance
Business Strategy
02.
70% of small businesses are unprepared against cyber attacks.


